Intro

Hi, I’m Jeff Schwartzentruber — a Staff Machine Learning Scientist at eSentire and a builder-manager who ships high-reliability AI for cybersecurity. I design and deploy production GenAI systems in the SOC—LLMs with RAG, tool-use, and agentic orchestration—that automate investigations, raise detection fidelity, and close the analyst feedback loop. My focus is making AI safe, observable, and cost-efficient at scale.
Beyond industry, I serve as Adjunct Faculty at Dalhousie University and Special Graduate Faculty at the University of Guelph, co-leading research on unsupervised threat detection and log/graph analytics. I’m a CISSP and P.Eng., with 15+ years turning complex data and systems problems into measurable, operational outcomes.
- GenAI for Security: SOC-grade LLM platforms with RAG, toolchains, guardrails, evals, and red-teaming.
- AI Detection & Analytics: Unsupervised models, log abstraction, and graph-based threat attribution.
- Engineering Leadership: Profiling end-to-end bottlenecks, cutting latency, improving throughput, and building fault-tolerant pipelines.
Want the details? Explore my recent work and speaking/writing.
Work

Summary
I build production AI for cyber. My recent work centers on SOC-grade LLM platforms (RAG, tool-use, agentic orchestration) and unsupervised detection models that automate investigations, raise detection fidelity, and close the analyst feedback loop—with observability, safety, and cost efficiency baked in. I also co-lead academic research in threat analytics and mentor startups on secure-by-design GenAI adoption. Highlights below.
SOC-Grade LLM Platform (MDR)

Designed and deployed production LLM capabilities inside the SOC to automate investigation steps and summarize outcomes for analysts.
- RAG + tool-calling pipelines with guardrails and eval harnesses; agentic orchestration for multi-step investigations.
- Human-in-the-loop feedback integrated to continuously improve precision/recall and analyst trust.
- End-to-end profiling to cut inference latency and cost without sacrificing safety.
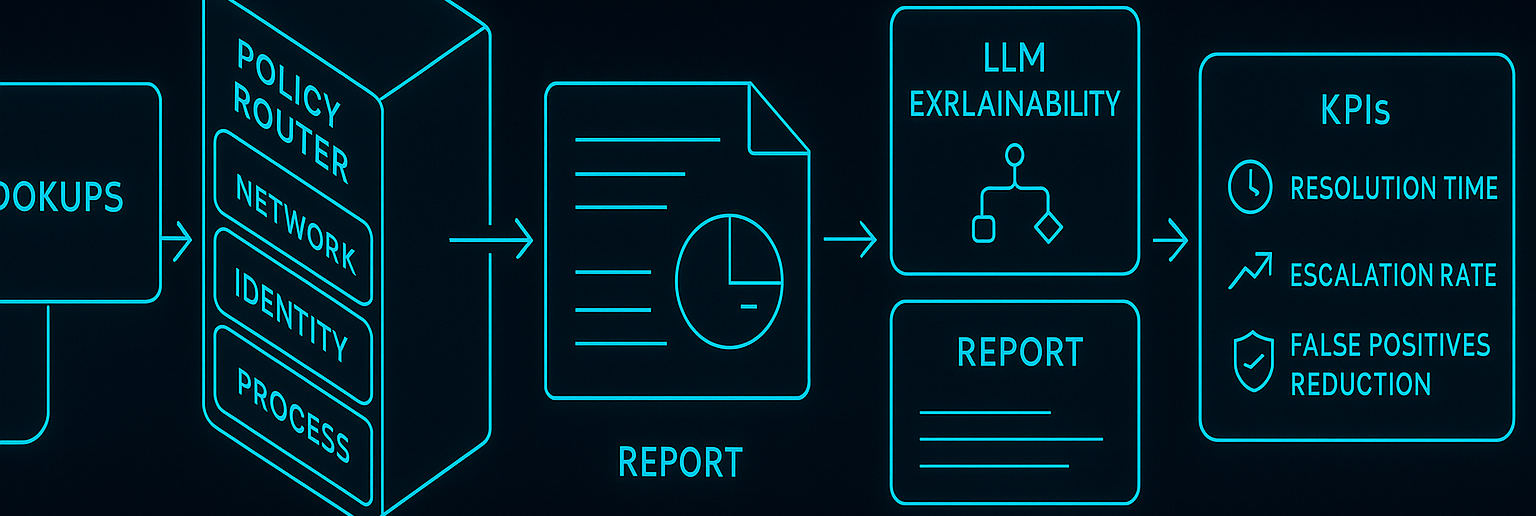
Automated Investigation & Analyst Copilot Services

Production services that triage alerts, perform structured lookups, and generate defensible investigation reports.
- Composable handlers for enrichment (process, network, identity) with policy-driven routing.
- LLM explainability, error tracing, and audit artifacts to support SOC reviews.
- Operational KPIs: resolution time, escalation rate, and false-positive reduction.
Unsupervised Threat Detection & Log Abstraction
Academic/industry research on learning patterns directly from heterogeneous telemetry—minimizing brittle normalization layers and enabling broader coverage across SIEM/NDR/EDR sources. See the ARES paper Log Abstraction for Information Security: Heuristics and Reproducibility.
Graph-Based Threat Analytics

University collaborations applying graph theory + ML to attribute behaviors and surface campaign-level patterns across noisy security data. Focus areas: entity resolution, rare-path detection, and high-precision clustering for IR.
GenAI Risk & Secure-by-Design Advisory

Advisor to startups and programs on GenAI safety, policy, and architecture: data governance, prompt/response controls, red-teaming, and supply-chain hygiene for LLM applications.
Earlier Work (Archive)
TPO for HR Operational Intelligence
Co-founded an AI startup delivering Tailored Process Optimization for attrition risk and retention strategy.
Intelligent Nozzle Design using ML
Genetic-algorithm optimization for abrasive waterjet machining; presented at the 23rd International Conference on Waterjetting.
AI Winglet Design
MATLAB + CFD loop to auto-design winglets for improved lift-to-drag; ~12% performance gain in simulations.
If any of this sparks your interest—or you’d like a deeper dive into platform design, evals, or guardrails—feel free to contact me.
About

I’m a Canada-based Staff Machine Learning Scientist focused on AI for cyber. I also serve as Adjunct Faculty (Dalhousie Computer Science) and Special Graduate Faculty (University of Guelph), co-supervising research at the ML–security boundary. Degrees: PhD, MASc, and BEng. I’m a CISSP and P.Eng. with a builder–manager ethos: ship reliable AI, measure rigorously, and make it safe, observable, and cost-efficient in production. Website · LinkedIn.
Peer-Reviewed Publications
- Rabieinejad, Dehghantanha, Zarrinkalam, Schwartzentruber (2025). United We Log, Divided We Identify: A Decentralized Approach for Automated Log Analysis, ACNS Workshops. DOI
- Rabieinejad, Zarrinkalam, Dehghantanha, Schwartzentruber (2025). Threattracer: A Novel Graph-Based Automation for APT Modeling and Attribution, SSRN. DOI
- Qiu, Zhou, Niblett, Johnston, Schwartzentruber, Zincir-Heywood, Heywood (2024). BoW vs. word-vector embeddings for anomaly detection in logs, Int’l Journal of Network Management.
- Copstein, Niblett, Johnston, Schwartzentruber, Heywood, Zincir-Heywood (2023). MIMC: Anomaly Detection in Network Data via Multiple Instances of Micro-Cluster Detection, IEEE CNSM.
- Copstein, Niblett, Johnston, Schwartzentruber, Heywood, Zincir-Heywood (2023). Towards Anomaly Detection using Multiple Instances of Micro-Cluster Detection, IEEE CSNet.
- Kashef, Freunek, Schwartzentruber, Samavi, Bulgurcu, Khan, Santos (2023). Bridging the Bubbles: Connecting Academia and Industry in Cybersecurity Research, IEEE SecDev.
- Copstein, Karlsen, Schwartzentruber, Zincir-Heywood, Heywood (2022). Exploring Syntactical Features for Anomaly Detection in Application Logs, it – Information Technology.
- Copstein, Schwartzentruber, Zincir-Heywood, Heywood (2021). Log Abstraction for Information Security, ARES 2021. Link
- Schwartzentruber, Papini, Spelt (2018). Characterizing and Modelling Delamination … Abrasive Waterjet Cutting, Composites Part A.
- Schwartzentruber, Papini, Spelt (2018). Modelling of Delamination due to Hydraulic Shock …, Int’l Journal of Machine Tools and Manufacture. Link
- Haghbin, Khakpour, Schwartzentruber, Papini (2018). Measurement of Abrasive Particle Velocity …, Journal of Materials Processing Technology.
- Schwartzentruber, Spelt, Papini (2017). Prediction of Surface Roughness …, Int’l Journal of Machine Tools and Manufacture. Link
- Schwartzentruber (2017). A Usability Study for EFB Flight Planning Apps on Tablets, IJAAA. Link
- Kowsari, Schwartzentruber, Spelt, Papini (2017). Erosive smoothing of abrasive slurry-jet micro-machined channels …, Precision Engineering. Journal
- Schwartzentruber, Narayanan, Liu, Papini (2016). Optimized abrasive waterjet nozzle design using genetic algorithms, 23rd Int’l Conf. on Water Jetting. Link
- Schwartzentruber, Papini, Spelt (2015). Abrasive Waterjet Machining Small Features in Composite Materials, 20th ICCM.
- Schwartzentruber, Papini (2014). Abrasive Waterjet Micro-Piercing of Borosilicate Glass, Journal of Materials Processing Technology. Link
Media & Press
- The Evolution of AI in Cyber Security — MLOps Podcast (2025). Listen
- AI may be a powerful tool, but it’s no substitute for cyber experts — Toronto Star (2025). Read
- Agentic AI-Powered Payments Demand a New Kind of Oversight — AI Journal (2025). Read
- AI in everyday tech brings hidden cybersecurity risks — The Globe and Mail (2025). Read
- Agents are here — but can you see what they’re doing? — CIO Magazine (2025). Read
- The Adoption of Digital Twin Technology Comes with Cybersecurity Concerns — Healthcare Business Today (2024). Read
- AI Cybersecurity Regulations and the Need for Corporate Culture Changes — HPCwire (2024). Read
- The Adoption of Digital Twin Technology Comes with Cybersecurity Concerns — C+S Engineer (2024). Read
- How Safe and Secure Is GenAI Really? — InformationWeek (2024). Read
- How to combat generative AI security risks — LeadDev (2024). Read
- Vibe coding security risks and how to mitigate them — IT Pro (2024).
For anything not linked above—or to request PDFs—feel free to contact me.
Contact
Elements
Text
This is bold and this is strong. This is italic and this is emphasized.
This is superscript text and this is subscript text.
This is underlined and this is code: for (;;) { ... }. Finally, this is a link.
Heading Level 2
Heading Level 3
Heading Level 4
Heading Level 5
Heading Level 6
Blockquote
Fringilla nisl. Donec accumsan interdum nisi, quis tincidunt felis sagittis eget tempus euismod. Vestibulum ante ipsum primis in faucibus vestibulum. Blandit adipiscing eu felis iaculis volutpat ac adipiscing accumsan faucibus. Vestibulum ante ipsum primis in faucibus lorem ipsum dolor sit amet nullam adipiscing eu felis.
Preformatted
i = 0;
while (!deck.isInOrder()) {
print 'Iteration ' + i;
deck.shuffle();
i++;
}
print 'It took ' + i + ' iterations to sort the deck.';
Lists
Unordered
- Dolor pulvinar etiam.
- Sagittis adipiscing.
- Felis enim feugiat.
Alternate
- Dolor pulvinar etiam.
- Sagittis adipiscing.
- Felis enim feugiat.
Ordered
- Dolor pulvinar etiam.
- Etiam vel felis viverra.
- Felis enim feugiat.
- Dolor pulvinar etiam.
- Etiam vel felis lorem.
- Felis enim et feugiat.
Icons
Actions
Table
Default
| Name |
Description |
Price |
| Item One |
Ante turpis integer aliquet porttitor. |
29.99 |
| Item Two |
Vis ac commodo adipiscing arcu aliquet. |
19.99 |
| Item Three |
Morbi faucibus arcu accumsan lorem. |
29.99 |
| Item Four |
Vitae integer tempus condimentum. |
19.99 |
| Item Five |
Ante turpis integer aliquet porttitor. |
29.99 |
|
100.00 |
Alternate
| Name |
Description |
Price |
| Item One |
Ante turpis integer aliquet porttitor. |
29.99 |
| Item Two |
Vis ac commodo adipiscing arcu aliquet. |
19.99 |
| Item Three |
Morbi faucibus arcu accumsan lorem. |
29.99 |
| Item Four |
Vitae integer tempus condimentum. |
19.99 |
| Item Five |
Ante turpis integer aliquet porttitor. |
29.99 |
|
100.00 |







